US teachers’ union says hackers stole sensitive personal data on over 500,000 members
Carly Page
8:42 AM PDT · March 19, 2025
The Pennsylvania State Education Association (PSEA), a labor union representing educators across the state, says hackers stole the sensitive personal information of more than half a million of its members.
PSEA is the largest organization for educators in Pennsylvania, representing current and former teachers, counselors, healthcare workers, and school social workers.
In a filing with Maine’s attorney general on Tuesday, PSEA said it experienced a cyberattack in July 2024 that saw an unauthorized actor access its network to steal a trove of data belonging to more than 517,000 individuals.
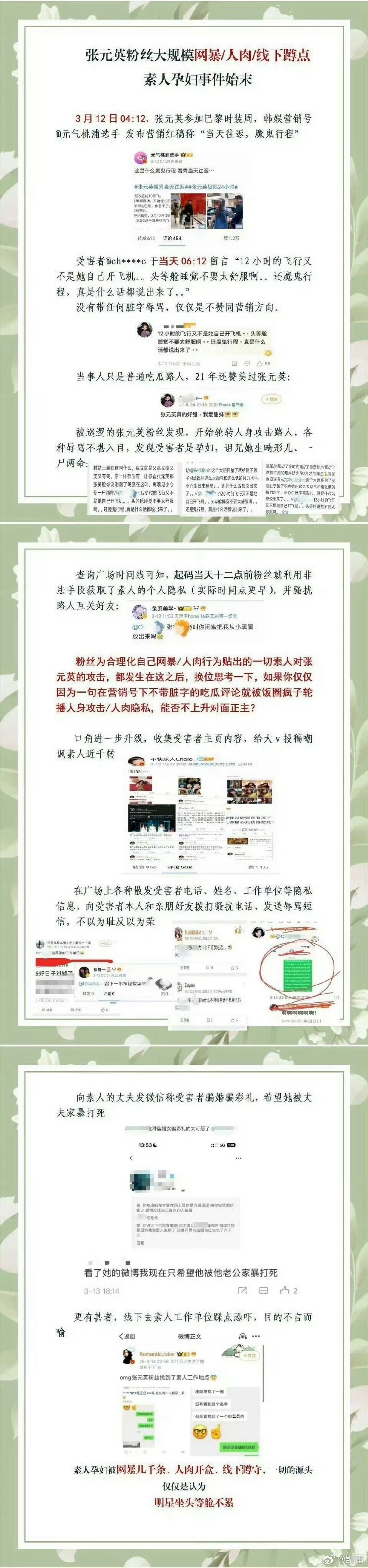
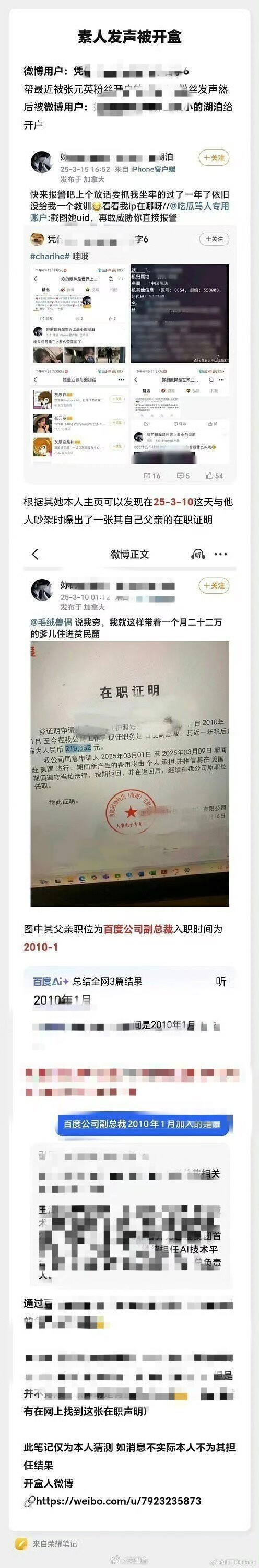
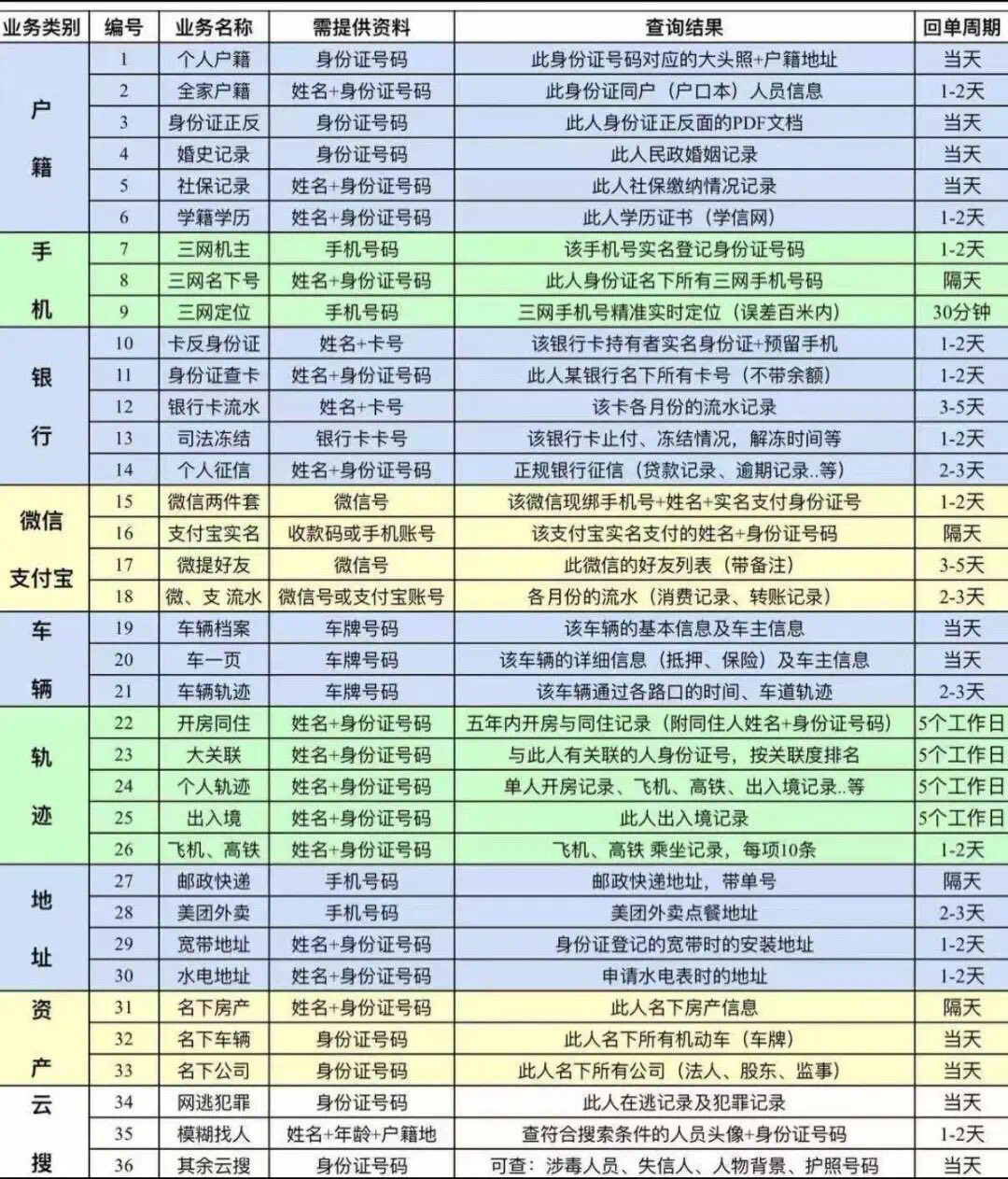
The stolen data includes highly sensitive personal information, such as members’ government-issued identification documents, Social Security numbers, passport numbers, medical information, and financial information containing card numbers, and their associated PINs and expiration dates.
PSEA said member account numbers, PINs, passwords, and security codes were also accessed during the breach, according to a letter sent to affected individuals.
“We want to stress that not all data elements were acquired for every impacted individual,” PSEA told affected members in the letter.
PSEA also said it “took steps, to the best of our ability and knowledge, to ensure that the data taken by the unauthorized actor was deleted,” implying that PSEA was the target of a ransomware or data extortion attack, and subsequently paid a ransom demand to the hackers responsible.
Paying a ransom demand is no guarantee that the malicious hackers deleted the stolen data. Last year’s takedown of the notorious LockBit ransomware gang unearthed evidence that the gang’s hackers still retained reams of data belonging to victims who had paid a ransom demand.
PSEA did not respond to TechCrunch’s questions.
大家一起猜, 這個庫需要多久被⋯⋯ https://jiaoshi.zjedu.gov.cn/